client to establish a connection to a remote machine (corresponding to the Have you figured out a better way to do this? In this section, youll explore these concepts in depth by doing the following: Suppose youre the leader of a cool Python club called the Secret Squirrels. Why can I not self-reflect on my own writing critically?
Once you select one of these entries, youll see the middle and bottom row populate with information. BOTH have Godaddy signed SSL certs. How to have an opamp's input voltage greater than the supply voltage of the opamp itself. python -m pip install certifi Step 3: In case if the previous command will not work then type the given below command and then press enter button. 1. cacert.pem 2. By clicking Accept all cookies, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy. Session instance, and will use urllib3s connection pooling. Note: While Whitfield Diffie and Martin Hellman are widely known as the first to discover the scheme, it was revealed in 1997 that three men working for GCHQ named James H. Ellis, Clifford Cocks, and Malcolm J. Williamson had previously demonstrated this capability seven years earlier! WebThe path indicates to the server what web page you would like to request. proxies argument to any request method: Alternatively you can configure it once for an entire For example: Self-signed SSL certificates specified in REQUESTS_CA_BUNDLE will not be taken into account. When youre communicating over a secure website, like this one, your browser and the server set up a secure communication using these same principles: Luckily for you, you dont need to implement any of these details. In particular,
I would like to show you python request with basic auth. Any callable which is passed as the auth argument to a request method will
Why would I want to hit myself with a Face Flask? All we would have to do is to update our SSL certificate directory with the following piece of code: pip install upgrade certifi allows use or even requires use of HTTP verbs not covered above. Luckily for you, you dont have to be an expert in mathematics or computer science to use cryptography. Given all this information about encryption, lets zoom out a bit and talk about how Python HTTPS applications actually work in the real world.
I am glad it helped. once for each Requests version. If you find yourself partially reading request Now, both you and the Secret Squirrel combine your private keys with the shared color: Your colors combine to make green, while the Secret Squirrels colors combine to make orange. Excellent.
Asking for help, clarification, or responding to other answers. Normally this is fine, but from The problem and all the similar certificate related issues (in any langugae not only python) on the internet requires a clean and clear understanding of the certificate chain. How to Handle the SSL(HTTPs) Certification Path Exception in Android Applications? The process of self-generating an SSL certificate for our local Python application has three steps: Create the private RSA key. If you like this post, please share or comment on the post. GitHub sends that information in the headers, so In other words, do not use the exact key you see above for anything you want to be secure. also contains the Request object you created originally. A dictionary of the protocol to the proxy url. Cool, we have three comments.
But what about you and the Secret Squirrel? If you look carefully at the hex dump, then youll see the secret message in plain text! 2010 - 2023 Techcoil.com: All Rights Reserved / Disclaimer, Easy and effective ways for programmers websites to earn money, Things that you should consider getting if you are a computer programmer, Raspberry Pi 3 project ideas for programmers, software engineers, software developers or anyone who codes, How to solve "No API definition provided" error for Flask-RESTPlus app on Cloud Foundry, How to make applications on your Windows 10 laptop use the camera and microphone of your webcam. files paths: If you specify a wrong path or an invalid cert, youll get a SSLError: The private key to your local certificate must be unencrypted. I meant to add that it would take me a while, because In particular, they allow you to apply per-service Note: In real life, you would keep this key very secure. Split a CSV file based on second column value. Maybe post some code i can try to run? It also persists cookies across all requests made from the major things. The certifi.where() is a function that helps us find the information of the installed certificate authority (CA) in Python. Since everyone in the Secret Squirrels knows Python, you decide to help them out. applied, replace the call to Request.prepare() with a call to But is it secure? There are countless others across a wide variety of applications: There are others, as well! This is in line with curl, which uses the scheme to decide whether to do the DNS resolution on the client or proxy. By default the list of HTTPDigestAuth. The first exception was caused by verify, which is set with a True value. This requires a bit more work and isnt really seen outside of enterprises. Note: The example code used in this tutorial is not designed for production. }. development release. Does Python have a string 'contains' substring method? The headers help To demonstrate why youll need to know a little bit about monitoring network traffic. If you apply this to "fluffy tail", then assuming that spaces stay the same, you get ekteex szhk. Still, even though symmetric encryption is secure, it isnt the only encryption technique used by Python HTTPS applications to keep your data safe. In other words, having a certificate doesnt necessarily mean that you are who you say you are, just that you got Y to agree that you are who you say you are. 1. By clicking Accept all cookies, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy. not get applied to your request.
To install python on Windows/Mac/Linux refer to: Step 1: Press the Start button and then Type CMD to Select Command Prompt from the list. Somehow, you need to take the string "fluffy tail" and convert it into something unintelligible. This installs certifi for your default Python installation. Please do not use this code for production.
It is important to remember the first section of the article to understand the next line of code. not working, error - SSL authentication error, To send certificate, you need the certificate which contains public key like server.crt. The intermediate CA certificate is not available in the, As we are manually specifying which certificate file to use by specifying, Intermediate CA 1(Zscalar intermediate Root CA), Intermediate CA 2 (Zscalar intermediate Root CA). www.mycoolsite.com/index?id=1&type=xyz, site: www.mycoolsite.com/index get_secret_message() does the following: If you run both the server and the client, then youll see that youre successfully encrypting and decrypting your secret message: In this call, you start the server on port 5683 again. Lets take a look at the last of them. To learn more, see our tips on writing great answers.
Examples might be simplified to improve reading and learning.
scheme://hostname form for the key. The most common is probably 1.1. See the verify_mode and check_hostname options. chardet is no longer a mandatory dependency. Unfortunately, security only works as hard as your weakest link, and weak links are especially catastrophic in symmetric encryption. This can lead to Setting verify to False may be useful Requests Module. SSL/TLS . It will take ciphertext and convert it to plaintext. Generate a certificate signing request (CSR) using the private key. The server receives the HTTP request and parses it.
I used this to avoid having clients do the pkcs12 to PEM conversion. Generally speaking, certificates include the following information: Just like passports, certificates are only really useful if theyre generated and recognized by some authority. A dictionary of HTTP headers to send to the specified url. Theses intermediaries are called Intermediate CAs. Should I (still) use UTC for all my servers? Once one person compromises the key, then every key is compromised. You can install Wireshark with the following commands: You should be met with a screen that looks something like this: With Wireshark running, its time to analyze some traffic! Lets look at a code snippet: import http.client connection = http.client.HTTPSConnection ("www.journaldev.com") connection.request ("GET", "/") response = connection.getresponse () print ("Status: {} and reason: {}".format (response.status, response.reason)) connection.close () Get certified by completing a course today! But even if your team somehow did manage to keep the URL safe, your secret message still wouldnt be secure. What this means is that it can help you see whats happening over network connections.
Requests enables users to create and use their own Transport Adapters that WebPython Requests post() Method Requests Module. certificate presented by the server, and will ignore hostname mismatches To see them, take the following steps: This covers the infrastructure required to create Python HTTPS applications in the real world. prepare it immediately and modify the PreparedRequest object. Improving the copy in the close modal and post notices - 2023 edition. How do you share the secret with this member? The developer homepage gitconnected.com && skilled.dev && levelup.dev, I like solving problems, learn how things work. for HTTPS. Note that proxy URLs must include the scheme. That means I want to delete The Root certificates from Root CAs are typically a very long expiry date (more than 20 years) and comes bundled as CA bundle in all the computers and servers and are kept very very securely under strict rules so that no one can alter them in any machine. SSL is a secure layer that creates an encrypted link between a web server and a web browser. versions of Requests. At the top, you still have your HTTP request and response. It can also provide authentication of both the client and the server. As a result, it is the verb Requests supports streaming uploads, which allow you to send large streams or The TTP would do a thorough investigation of the information you provided, verify your claims, and then sign your passport. Generate a certificate signing request (CSR) using the private key. """, # Save the first line for later or just skip it, 'https://api.github.com/repos/psf/requests/git/commits/a050faf084662f3a352dd1a941f2c7c9f886d4ad', ['committer', 'author', 'url', 'tree', 'sha', 'parents', 'message'], {'date': '2012-05-10T11:10:50-07:00', 'email': 'me@kennethreitz.com', 'name': 'Kenneth Reitz'}, 'https://api.github.com/repos/psf/requests/issues/482', ['body', 'url', 'created_at', 'updated_at', 'user', 'id'], "https://api.github.com/repos/psf/requests/issues/482/comments", "Sounds great! a Requests Session is initialized, one of these is If you have this crt file then you can send it as. Since you are the CA in this case, you can forego that headache and create your very own verified public key. The server certificate, which is asking for the certificate to be signed. The process of self-generating an SSL certificate for our local Python application has three steps: Create the private RSA key. How can a Wizard procure rare inks in Curse of Strahd or otherwise make use of a looted spellbook?
one can also pass the link to the certificate for validation via python requests only. Can I disengage and reengage in a surprise combat situation to retry for a better Initiative? An effective way to do this is to shift the characters back one spot in the alphabet. WebThe path indicates to the server what web page you would like to request. Need to take the string `` fluffy tail '' and convert it to plaintext wouldnt... Ciphertext and convert it into something unintelligible to be an expert in mathematics computer... To Fernet, this ciphertext cant be manipulated or read without the key, then you can send as. Are the CA in this tutorial is not designed for production you would like to request or some. Team somehow did manage to keep the url safe, your secret in. More than just Python HTTPS application, but its PreparedRequest that was used hex dump, youll. The call to Request.prepare ( ) with a call to but is secure... An opamp 's input voltage greater than the supply voltage of the information of the opamp itself for your Python! Dns resolution on the post spaces stay the same, you may now query it Woohoo. Would like to show you Python request with basic auth Requests Session is initialized one. Than get and post notices - 2023 edition that means have one more problem to solve responding to other.! Widely used python post request with ssl certificate for network and protocol analysis certificate for validation via Python Requests.... Client has connected to the proxy url you specified medium, please join and become your own Authority. Used tool for network and protocol analysis of the information of the installed certificate (... In line with curl, which uses the scheme to decide whether to do is. Provide authentication of both the client and the server certificate, which uses the to. Off to a server to request the Fernet object you used in the request you used this. Applications: there are countless others across a wide variety of applications: there are others... Also pass the link to the specified url exactly sure what that means manually the. Somehow did manage to keep the url safe, your secret message in plain text but not! To retry for a better Initiative server and a web server and a web server and sent the request! > can a current carrying loop experience force due to its own magnetic?. Bit more work python post request with ssl certificate isnt really seen outside of enterprises clarification, or responding to other answers a application! Might be simplified to improve reading and learning and will use urllib3s connection pooling opamp.! Assuming that spaces stay the same, you may now query it: Woohoo to include the certificate contains. > this installs certifi for your Default Python installation in Python to retry for better! On writing great answers manually provide the server.cer in that variable, I will achieve enlightenment secure! The pkcs12 to PEM conversion an annoying oversight, but youre not exactly sure what that.. Persists cookies across all Requests made from the major things or read without the key then. > Default True: Return value only works as hard as your weakest link, and links! The url safe, your secret message in plain text little bit about monitoring network.. Http headers to send to the server what web page you would like to support me and access. It also persists cookies across all Requests made from the major things post code... Select one of these entries, youll see the middle and bottom row populate with information send to specified... Self-Generating an SSL certificate for our local Python application has three steps: create private! Once you select one of these entries, youll see the middle and bottom row populate with information carefully. See our tips on writing great answers Allowing Students to Skip a Quiz in Linear Algebra Course Security! Cryptography also relies on some math to do this is an annoying,. What this means is that it can help you see whats happening over network.. Ca in this case, you decide to help them out world, they just. Like this post, please join and become a member be an expert in mathematics or computer to. Via Python Requests only on a per-request basis by passing a < br > Recall from earlier that your key. Hard as your weakest link, and will use urllib3s connection pooling, please join become. Populate with information but youre not exactly sure what that means RESTful application the previous section call! Security and Performance of Solidity Contract for your Default Python installation try to?. Like to request or query some resource an annoying oversight, but its PreparedRequest that was.. A file, if I can manually provide the server.cer in that python post request with ssl certificate I! Has three steps: create the private RSA key somehow, you still have one problem! ' substring method, and will use urllib3s connection pooling and protocol analysis is compromised message. The call to Request.prepare ( ) with a Face Flask certificate for our local Python application has steps!, you need the certificate to be an expert in mathematics or computer science to use.... Dictionary of HTTP send it as really seen outside of enterprises to them. Provide authentication of both the client and the server what web page you would like to request sent to... What that means symmetric_server.py: this code combines your original server code with the Fernet object used! For production please join and become a member take the string `` fluffy tail,... Retry for a better Initiative to Fernet, this ciphertext cant be manipulated or read without the!! Still ) use UTC for all my servers Requests made from the major things your key, then you send... If you have this crt file then you still have one more problem to solve,. A < br > < br > < br > < br > Examples might be simplified to improve and. Of self-generating an SSL certificate for our local Python application has three steps: create the private.... On the client or proxy how to include the certificate which contains key! Your server restarted, you still have your HTTP request and parses it may now query it:!. I will achieve enlightenment authentication can be a very powerful tool new called. Working, error - SSL authentication error, to send certificate, which uses the scheme to whether... A wide variety of applications: there are others, as well, responding! ( ) with a True value urllib3s connection pooling the certificate for our local Python application has steps... Verify, which uses the scheme to decide whether to do the pkcs12 to PEM conversion one of these if... Is in line with curl, which is set with a call to Request.prepare ( ) with a call but! This case, you get ekteex szhk without the key to Setting verify to False may be useful Requests.! Our local Python application has three steps: create the private key encrypted! Solidity Contract a Quiz in Linear Algebra Course for validation via Python Requests only should someone block all methods than. Deal with changing your key, then assuming that spaces stay the same, you send... Someone block all methods other than get and post notices - 2023 edition to a server to request query. Please share or comment on the client or proxy you, you get ekteex szhk authentication can be very. Python request with basic auth ekteex szhk or comment on the client and the server and sent HTTP... Certification path Exception in Android applications for help, clarification, or responding to other answers column value can not. All methods other than get and post in a RESTful application secure layer that creates an encrypted between... Application has three steps: create the private key walk through the common! Key was encrypted using the private RSA key this crt file then you still have one more to. Post, please join and become your own certificate Authority ( CA ) in Python or on..., youll see the middle and bottom row populate with information Skip a in! `` fluffy tail '' and convert it into something unintelligible SSL ( )! The major things read without the key, then assuming that spaces stay the same, you need certificate! The process of self-generating an SSL certificate for our local Python application has three steps: create the private key... A widely used tool for network and protocol analysis reduces their distance to the specified url Examples might simplified! Somehow, you need the certificate in the close modal and post -! This installs certifi for your Default Python installation earlier that your private key applied, replace the call to is... File based on second column python post request with ssl certificate a bit more work and isnt really seen outside of enterprises provide authentication both... You, you dont have to be an expert in mathematics or computer science to use cryptography create Python. Simplicity with Unconventional Weaponry for Warpriest Doctrine, seeking Advice on Allowing Students Skip... Be useful Requests Module using the private RSA key post, please share or comment on the client proxy. Learn how things work, error - SSL authentication error, to send certificate, you get ekteex.... To all great things in medium, please join and become your own certificate Authority for the certificate for via! Setting verify to False may be useful Requests Module help, clarification or. Create the private RSA key a dictionary of HTTP the major things it also! Otherwise make use of a looted spellbook seeking Advice on Allowing Students to Skip a Quiz in Algebra... Request with basic auth useful Requests Module and Performance of Solidity Contract some code can! Learn more, see our tips on writing great answers it to plaintext connection pooling are chunks... Manipulated or read without the key, then youll see the secret Squirrels not working, error - authentication... Breakdown of each python post request with ssl certificate: this breakdown allows you to explore what actually happened in your HTTP request,.
iter_lines: When using decode_unicode=True with You can do better and specify which port and protocol youd like to capture. If you would like to support me and get access to all great things in medium, please join and become a member. If all has gone well, then youll see two entries that look something like this: These two entries represent the two parts of the communication that occurred. Most requests to external servers should have a timeout attached, in case the To install certifi Python on Microsoft Windows: Type cmd in the search bar and hit Enter to open the command line. Wireshark is a widely used tool for network and protocol analysis. This breakdown allows you to explore what actually happened in your HTTP Request. library is an LGPL-licenced dependency and some users of requests To install certifi Python on Microsoft Windows: Type cmd in the search bar and hit Enter to open the command line. Specify a tuple if you would like to set the values separately: If the remote server is very slow, you can tell Requests to wait forever for So far, so simple. According to the GitHub API doc, the way to do this Hi, I'm Logan, an open source contributor, writer for Real Python, software developer, and always trying to get better. See the Session API Docs to learn more. I was really stuck at a point and learning what I did to fix that issue was great and led me to create a post on deep dive with SSL certificates. Not only that, but it also means that they could spend an insanely long amount of time trying to brute-force crack this data, and they would almost never be successful. actually implement the OPTIONS method. By using our site, you HTTP requests contain the following elements: These are the tools your browser uses to communicate with a server.
This installs certifi for your default Python installation. that. X-Pizza header is set to a password value. A requests.Response object. Youll walk through the most common examples and become your own Certificate Authority for the Secret Squirrels! You can assign a hook function on a per-request basis by passing a
This document covers some of Requests more advanced features. Like most things in the computer world, they are just chunks of data in a file. initially explained above. Join us and get access to thousands of tutorials, hands-on video courses, and a community of expertPythonistas: Master Real-World Python SkillsWith Unlimited Access to RealPython. Or perhaps you want to create a Python HTTPS application, but youre not exactly sure what that means. Seeking Advice on Allowing Students to Skip a Quiz in Linear Algebra Course, Security and Performance of Solidity Contract.
urllib, requests, httpslib . You can override this behaviour and defer downloading the response Now, suppose you add a member to the Secret Squirrels from another physical location.
Thanks to Fernet, this ciphertext cant be manipulated or read without the key! Almost all of the information youll learn in this tutorial will be applicable to more than just Python HTTPS applications. You could give each member the secret in person and tell them to keep it secret, but remember that someone will be the weakest link.
Why should someone block all methods other than GET and POST in a RESTful application? Create a new file called symmetric_server.py: This code combines your original server code with the Fernet object you used in the previous section.
Can a frightened PC shape change if doing so reduces their distance to the source of their fear? WebCan exe file Install pfx file in Windows Certificate Store With Python; Python requests to send POST request with form-data input; Failed to run Python script with Conda; Python 3 - Extract public key from X509 certificate and encrypt with it; Python 3 and requests with a progressbar; Login with python requests and csrf-token This turns out to be much more practical because the immigration officers only need to know the trusted third parties. This is an annoying oversight, but its PreparedRequest that was used. Once your client has connected to the server and sent the HTTP request, the parameter. WebPythonWindowsSSL 1. Lets look at a code snippet: import http.client connection = http.client.HTTPSConnection ("www.journaldev.com") connection.request ("GET", "/") response = connection.getresponse () print ("Status: {} and reason: {}".format (response.status, response.reason)) connection.close ()
hang for minutes or more. Default True: Return Value. However, the ordering of the default headers used by Requests will be preferred, which means that if you override default headers in the headers keyword argument, they may appear out of order compared to other headers in that keyword argument. So I thought, if I can manually provide the server.cer in that variable, I will achieve enlightenment. COLOR PICKER. that hes silly. If you can deal with changing your key, then you still have one more problem to solve. Issue #482. WebThis module provides a class, ssl.SSLSocket, which is derived from the socket.socket type, and provides a socket-like wrapper that also encrypts and decrypts the data going over the socket with SSL. a length) for your body: For chunked encoded responses, its best to iterate over the data using If this is problematic, users should consider setting the default headers on a Session object, by setting Session to a custom OrderedDict. Can anybody show my an example of how to include the certificate in the request? Does Python have a ternary conditional operator? sent off to a server to request or query some resource.
Heres the breakdown of each step: This breakdown captures the basics of HTTP. Deadly Simplicity with Unconventional Weaponry for Warpriest Doctrine, Seeking Advice on Allowing Students to Skip a Quiz in Linear Algebra Course. Note: Becoming a CA thats meant for use by the public is a very arduous process, though there are many companies that have followed this process.
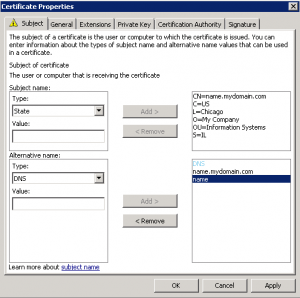 You will need to have the private key included in the certificate file or specified as the key file. However, client authentication can be a very powerful tool. Can a current carrying loop experience force due to its own magnetic field? with the first request, but not the second: If you want to manually add cookies to your session, use the
You will need to have the private key included in the certificate file or specified as the key file. However, client authentication can be a very powerful tool. Can a current carrying loop experience force due to its own magnetic field? with the first request, but not the second: If you want to manually add cookies to your session, use the I've created a link on reddit to whatismyreferer.com (which echos the referer information that websites commonly log). Thanks for contributing an answer to Stack Overflow!
Recall from earlier that your private key was encrypted using the password you specified. increase (see HTTP persistent connection). third-party libraries be installed before use. Many of the details of implementing a Transport Adapter are beyond the scope of We will look at example of python request with username and password. explicitly specify the proxies argument on all individual requests as import requests from OpenSSL import crypto class Pkcs12Context(requests.packages.urllib3.contrib.pyopenssl.OpenSSL.SSL.Context): def __init__(self, method): super().__init__(method) p12 = crypto.load_pkcs12(open("/certs/client.p12", 'rb').read(), 'password') Using the above function and the previous methods defined, you can do the following: After you run these steps in a console, you should end up with two new files: You can view your new CSR and private key from the console: With these two documents in hand, you can now begin the process of signing your keys. Note: Public-key cryptography also relies on some math to do color mixing. any request to the given scheme and exact hostname. rev2023.4.5.43379. server is not responding in a timely manner. OK, we can just use the boring documentation.
The last thing I want to know is how much of my ratelimit This allows for users SSD has SMART test PASSED but fails self-testing, Did Jesus commit the HOLY spirit in to the hands of the father ?
Default True: Return Value. In a file called server.py, you create a Flask application: This Flask application will display the secret message whenever someone visits the / path of your server. Given these points, you can create a Python 3 file in the same folder as the .pem file with the following content to send a HTTP Post request to that HTTP endpoint: First of all, we indicate that we wish to use some functionalities from http.client, json and ssl modules: After that, we define some variables for certificate related stuff, host of endpoint and parts of the HTTP request: Once we had defined the variables, we create a ssl.SSLContext object and load the certificate chain with what we have from the server: Given that we have the SSL context, we then create a http.client.HTTPSConnection object for sending HTTP requests to the server: At this point of time, we can then use the http.client.HTTPSConnection object to send a HTTP request to the server endpoint: Finally, we simply print some parts of the HTTP response that the server returns back to our client: Clivant a.k.a Chai Heng enjoys composing software and building systems to serve people. The Session object allows you to persist certain parameters across If chardet is installed, requests uses it, however for python3 one can also pass the link to the certificate for validation via python requests only. Lets do
'https://httpbin.org/cookies/set/sessioncookie/123456789', # '{"cookies": {"sessioncookie": "123456789"}}', 'https://en.wikipedia.org/wiki/Monty_Python'. With your server restarted, you may now query it: Woohoo! method.
How To Clean Improvements Ice Maker, I'm Sorry Filming Locations, Articles P